How to secure iPhone data with pair locking and supervision
In this article we're going to take a closer look at an obscure but highly effective way of increasing your phone's security: pair-locking.
What is pairing?
Pairing creates a trusted connection between your iPhone and a computer. For example, when you connect your iPhone to a computer with a USB cable, you are asked to grant full access, and once accepted, pairing takes place and a trusted key is kept for future connections. A connection is created between your iPhone and your computer so that applications like iTunes can communicate with your device. The bad news is that forensic applications that might harvest your data can use the same connection key to remotely communicate with your iPhone.
Once an iPhone is paired with a computer, that computer will have full access to all the personal information stored on your device. This means the computer can gain access to all photos, notes, videos, messages, and -- with the right knowledge -- hackers can even break passwords from third-party applications. Your iPhone can be accessed even when it's locked with a PIN code.
What is pair-locking?
Pair-locking your iPhone allows you to block any forensic application that tries to communicate with your iOS device, by preventing new pairings. You're pairing it with a single computer -- yours -- and preventing it from ever pairing with any other.
Pair-locking your iPhone requires you to erase all data from your device. For this reason, we recommend only pair-locking new phones, or creating a backup of your iPhone before pair-locking.
Is your iPhone paired with your computer already?
A private key is created when you pair your iPhone to a computer. This key is stored both on your iPhone and on the computer you have paired with. You can find a pairing record of your device easily, by doing the following:
- On macOS, open Terminal and paste the following:
open /var/db/lockdown - If you are using Windows, go to
%ProgramData%/Apple/lockdownin Explorer
Steps you need to take to pair-lock your iPhone
-
Download Apple Configurator from the App store on your Mac and open it
Connect your iPhone to your computer via USB, select your iPhone in Apple Configurator, and click "Prepare"
![Apple Configurator's "Prepare" button Apple Configurator's "Prepare" button]()
Apple Configurator's "Prepare" button Select
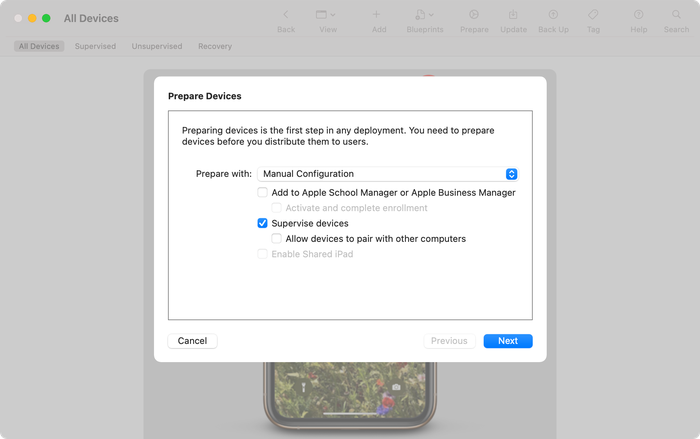
Manual Configurationfrom the dropdown, then checkSupervise devicesand uncheckAllow devices to pair with other computers![Make sure you uncheck the box to prevent pairing with other computers Make sure you uncheck the box to prevent pairing with other computers]()
Make sure you uncheck the box to prevent pairing with other computers -
Click
NextselectDo not enroll in MDMfrom the dropdown, then hitNextagain. - Hit
Skipwhen asked for your Apple ID, and choose any name you would like to 'create an organization'. - Click next, then click
Prepare. You'll need to enter your administrator password at this point, and you'll get a warning message explaining that all data will be erased from your device if you proceed. Make sure you have any data from your iPhone backed up before you proceed.
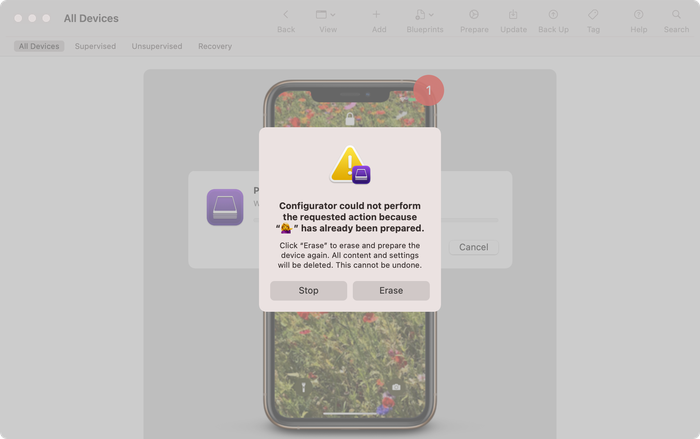
![Apple configurator may state that your device has already been prepared Apple configurator may state that your device has already been prepared]()
Apple configurator may state that your device has already been prepared
Just remember: if you do this, you won't be able to sync or connect your iPhone with any other computer. But neither will the bad guys.