FacebookはiPhoneバックアップに安全でない認証トークンを保存します

先月かそこらで、セキュリティの弱点とiPhoneの追跡に関して、少数のiOSアプリが注目されてきました。問題は、LinkedIn、Dropbox、これらのサイトを使用してiOSでユーザーを認証するアプリなど、他の多くのソーシャルネットワークサイトに当てはまりますが、Facebookの番です。
セキュリティ研究者のGareth Wrightは、FacebookのiOSアプリが認証トークンをプレーンテキストファイルに保持していることを発見しました。これらのトークンは、ログインに使用するパスワードと同等です。
バックアップに認証トークンを保存することは必ずしも悪い考えではありません。結局のところ、バックアップから携帯電話を復元する必要がある場合は、すべてがそのままログインされているのを見るのは良いことであり、これを行うにはトークンが必要です。 Facebookの現在の実装でこれがどのように機能するかを確認できます。
- iPhoneでFacebookアプリにログインし、iTunesでバックアップします
- iPhoneのFacebookアプリからログアウトします(左側のメニューの下部に移動し、[
Settings→Log Out]をクリックします) - iTunesバックアップを携帯電話に復元する
再びログインしていることがわかります。
地獄への道は善意で舗装されています
Facebookが認証トークンをバックアップに保存するかどうかは、主な問題ではありません。ここでの最大の問題は、トークンが暗号化されて おらず、デバイス固有の要素 がなく、時間制限がないことです。つまり、誰かがあなたのバックアップからファイルを引き出して、自分のデバイスにインポートできるということです。簡単に言えば、このファイルにアクセスできる人は誰でも、Facebookアカウントへのフルアクセスを持ち、それを使用してIDを盗んだり、アクティビティを追跡したりできます。
これに加えて、多くのサードパーティのアプリとサービスはFacebookを認証サービスとして使用しています。ハッカーが既にFacebookアカウントにサインインしている場合、ハッカーはそれを使用してこれらのサービスにアクセスすることもできます。
Facebookは、以下のコメントで通信社に返信しましたが、最も簡単な方法と思われる安全でないバックアップハッキングの可能性を省いているようです。
FacebookのiOSおよびAndroidアプリケーションは、製造元が提供するオペレーティングシステムでのみ使用することを目的としており、アクセストークンは、モバイルOSを変更した場合(つまり、ジェイルブレイクしたiOSまたは改造したAndroid)または物理デバイスへの悪意のあるアクターアクセスを許可した場合にのみ脆弱です。改変されていないバージョンのモバイルオペレーティングシステムでアプリケーションを開発およびテストし、開発、展開、セキュリティの基盤としてネイティブ保護に依存しています。これらはすべてジェイルブレイクされたデバイスで侵害されます。 Appleが述べているように、「iOSの無許可の変更により、ハッカーが個人情報を盗んだり、マルウェアやウイルスを導入したりする可能性があります。」自分自身を保護するために、すべてのユーザーがモバイルOSの変更を控えて、アプリケーションの不安定性やセキュリティの問題を防ぐことをお勧めします。
心配する必要がありますか?このファイルを取得するには、暗号化されていないバックアップが保存されているiOSデバイスまたはPCに物理的にアクセスできる必要があります。カジュアルなハッカーはそれらにアクセスできないかもしれませんが、決心したハッカーはそのようなアクセスを手配できるかもしれません。
明らかに、Facebookなどのアプリ発行元は、次の点で役立ちます。
- バックアップの認証トークンに追加の暗号化を適用します
- 他のデバイスで使用できないように、トークンにデバイス固有の要素があることを確認します
- トークンの有効期限が近い将来に設定されます
- 復元されたトークンからサービスへの新しいログインをユーザーに警告する
自分のFacebook認証トークンを調べたいですか?
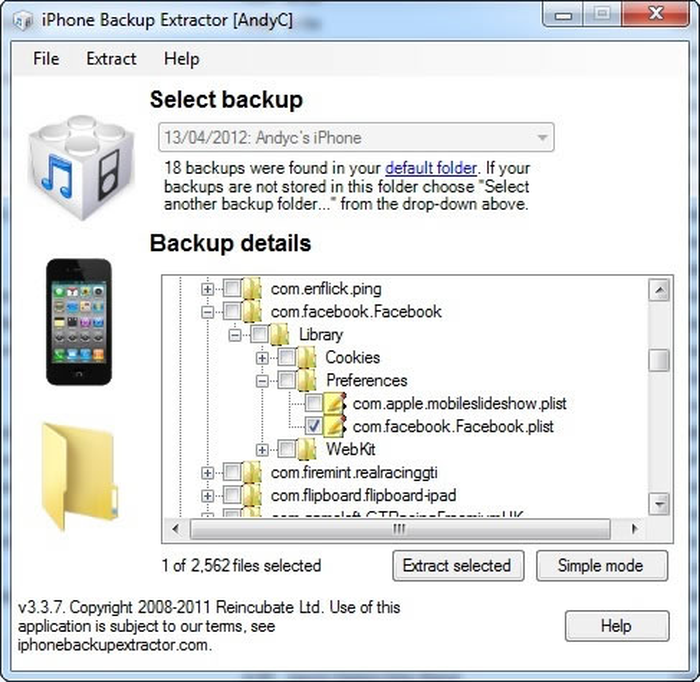
これを行うには、iPhone Backup Extractorを使用し、「エキスパートモード」でバックアップにアクセスします。あなたが何をしているかわからない限り、データを読んだり、Facebookにサインインしたりすることはできません。それを把握します。

